POODLE and You
The flaw would allow an attacker to steal certain information, such as session cookies, while you are using the browser. Mobile users (laptops and smartphones) are particularly vulnerable when using public wifi networks. While the browsers promise a fix in their next releases, it’s recommended you immediately turn off SSL3 support in your browser to guard against this exploit. Web server admins should disable SSL3 support in their configurations.
An easy test to check your browser is available. Just visit PoodleTest.com
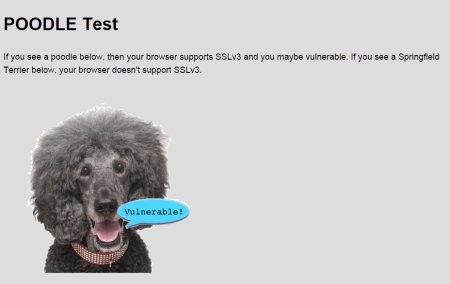
Despite sounding like a recent, advanced version, SSL3 is actually an older, legacy protocol, replaced by TLS 1.1, and the newer TLS 1.2 security protocols.
As we’ve discussed before, the best defense for this and other vulnerabilities is to use the latest version of your preferred browser, and keep it updated via automatic updates. All browsers are anticipated to guard against POODLE in their next releases, typically within 30 days.
To protect yourself now, you can update your browser configuration to remove support for the vulnerable SSL3 protocol.
IE is the easiest. Go to Internet Options > Advanced. Scroll down and uncheck the SSL3 box.

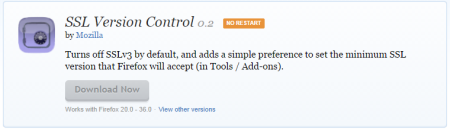
Firefox users can download an addon that will disable SSL3 from Mozilla: https://addons.mozilla.org/en-US/firefox/addon/ssl-version-control/
Unfortunately Chrome and Safari have not made it so easy to update their configurations. A nice summary with server and browser instructions is available at: http://scotthel.me/poodle
A good overview of the problem is available from Mozilla - “The POODLE Attack and the End of SSL 3.0